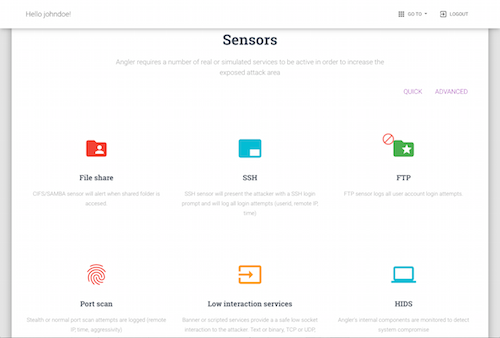
Sensors
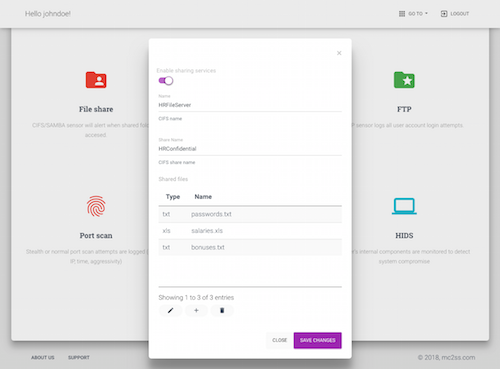
Port scan detection, file share, ftp, ssh and a large number of low interaction services
API for lure development and third party integration

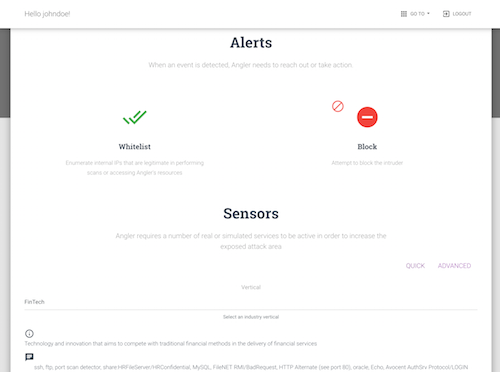
The device detects and captures new attacks and methods that are employed during attacker's lateral move. It advertises and exposes a configurable set of services that the attacker will inevitably explore. Additionally, the device monitors itself for compromise and port scan indication. When any IOC event is detected, it will be reported via email and/or syslog to the administrator. When enabled, the device can initiate an active response to the attacker's machine - ARP MITM.
The built in display will report the alert count and a blinking light will be active until the alerts are cleared.

If you require advanced analytics, fast SMS notifications or to remotely monitor your Angler devices, you need to subscribe to our secure managed service plan. If you do so at the device purchase time, then the device will be shipped to you preconfigured - just plug it into your network and forget about it. We will notify you whenever an IOC is detected or your device becomes unavailable due to connectivity issues.
Port scan detection, file share, ftp, ssh and a large number of low interaction services
API for lure development and third party integration
Built in email, syslog (SIEM integration), alert indicator and OLED display notification capability.
SMS - via secured managed service.
Built in web administration console, enabled for remote management via our secure managed service.
Quick setup and forget.
Embedded linux, quad-code 64bit 1GHz+ ARM, 1Gbps Ethernet, low consumption, OLED display
Angler is extremely easy to configure and deploy. Built in web console and the comprehensive 'verticals' templates eliminate the effort required when using open source solutions. Generally speaking, open sources solutions, while being a viable alternative, are easy to fingerprint and avoid. They do not have a built in management user interface and most are not under active development. Because of the long learning curve, creating and maintaining a honeypot that looks veritable, isn't easy, and the vast majority of organizations don't bother.
Angler is a complementary solution designed to fill the growing gaps in the conventional IDS that are plagued from false positives. When used together, it will dramatically improve the intrusion detection.
Yes, the device is designed not to require any external resources or access. Everything that is needed for the web configuration console, email and syslog notifications, is built in.
Angler employs techniques and methodologies that set it closer to a production honeypot.